Miscellaneous
Useful Utilities...
- Dependency Walker.
- Forgot your Windows admin password? Password reset ISO
- Diff-ext - A Windows Explorer context menu extension that allows to launch diff/merge tools on selected files.
HTTP Methods
Idempotent
... aside from error or expiration issues ... the side-effects of N > 0 identical requests is the same as for a single request ... The methods GET, HEAD, PUT and DELETE share this property. Also, the methods OPTIONS and TRACE ...
This means that the side effect of a request is identical whether 1 such request is sent or a million! A side effect might be changing a value in a database or uploading a file, for example.
On thing to notice in the above definition is that POST is not necessarily idempotent! I.e., two identical POST requests may have different side effects than a single such request. You'll see why in the section on this method.
GET
... retrieve whatever information ... is identified by the Request-URI. If the Request-URI refers to a data-producing process, it is the produced data which shall be returned ...
GET is idempotent because the request can be made any number of times but the content on the server will not change. I.e. the side effect is the same whether 1 or many requests are sent (there are no side effects).
From W3Schools:
- GET requests can be cached
- GET requests remain in the browser history
- GET requests can be bookmarked
- GET requests should never be used when dealing with sensitive data
- GET requests have length restrictions
- GET requests is only used to request data (not modify)
POST
... requests that the origin server accept the entity enclosed in the request as a new subordinate of the resource identified by the Request-URI...
"Subordinate" just indicates an "is contained/owned/part-of" relationship. E.g. a file is subordinate to a directory.
"Accept[ing] the enitity ... as a new subordinate" implies that whatever is POSTed is always added as new, which could, for example, be an append operation. Therefore, two such requests will not have the same side effect as one such event. In the former two objects could be added to, say, a list, and in the latter only one. Therefore POST need not be idempotent. In fact, one of the RFC examples is "extending a database through an append operation".
... The actual function performed by the POST method is determined by the server and is usually dependent on the Request-URI ...
In the POST request, and this is the reason for the non-idempotency, the URI
identifies the resource that will process/handle the message contents. Because the
processing is whatever the server likes, POSTs cannot guarantee idempotency, because the
server can do whatever it likes with the message contents... all that was specified was the
resource that operates on the contents! Think x++ - this is not idempotent.
From W3Schools:
- POST requests are never cached
- POST requests do not remain in the browser history
- POST requests cannot be bookmarked
- POST requests have no restrictions on data length
PUT
...The PUT method requests that the enclosed entity be stored under the supplied Request-URI ..
In a PUT request, the URI identifies the entity in the request, i.e., the message
contents. This is why idempotency is required. If we PUT the same uniquely identified thing
many times, we should still have one uniquely identified thing! Think x = 5 - this is idempotent.
DELETE
... requests that the origin server delete the resource identified by the Request-URI ...
Comms Shit
https://www.youtube.com/watch?v=OT04cEdpK-M https://www.youtube.com/watch?v=h_7d-m1ehoY https://www.youtube.com/watch?v=xn6lzrMJUDs - awesome intro to rf modulation from US army http://sss-mag.com/pdf/gmsk_tut.pdf http://www.seas.ucla.edu/brweb/teaching/ee215c_notes2.pdf https://books.google.co.uk/books?id=2CAqsF-RebgC&pg=PA110&redir_esc=y#v=onepage&q&f=false - erf https://www.youtube.com/watch?v=fSoXIqBlg9M - antennas
Angle modulation is a class of carrier modulation that is used in telecommunications transmission systems. The class comprises frequency modulation (FM) and phase modulation (PM), and is based on altering the frequency or the phase, respectively, of a carrier signal to encode the message signal.
In electrical engineering, a sinusoid with angle modulation can be decomposed into, or synthesized from, two amplitude-modulated sinusoids that are offset in phase by one-quarter cycle (pi/2 radians). All three functions have the same frequency. The amplitude modulated sinusoids are known as in-phase and quadrature components.
... every sinusoid can be expressed as the sum of a sine function (phase zero) and a cosine function (phase $\pi/2$). If the sine part is called the "in-phase" component, the cosine part can be called the "phase-quadrature" component. In general, "phase quadrature" means "90 degrees out of phase," i.e., a relative phase shift of $ \pm\pi/2$.
It is also the case that every sum of an in-phase and quadrature component can be expressed as a single sinusoid at some amplitude and phase....
http://www.comlab.hut.fi/opetus/333/2004_2005_slides/CarrierTimingRecovery.pdf
Miscrosoft Word Shortcut Keys
A summary of MS word keyboard shortcuts.
| Task | Key |
| Insert an empty field. | CTRL+F9 |
| Update selected fields. | F9 |
| Switch between a selected field code and its result. | SHIFT+F9 |
| Switch between all field codes and their results. | ALT+F9 |
| Change the selection to the Symbol font. | CTRL+SHIFT+Q |
| Apply subscript formatting (automatic spacing). | CTRL+EQUAL SIGN |
| Apply superscript formatting (automatic spacing). | CTRL+SHIFT+PLUS SIGN |
| Remove paragraph or character formatting. | CTRL+SPACEBAR |
Root Sumsung S3 Mini
Had some problems getting Kingo Root to connect to my phone. It seemed the driver installation would constantly fail. I tried various drivers but the one that worked for me was found here at Android XDA. The driver for "Samsung Galaxy S3 (all variants)" was the one that worked. For some reason the one for "Samsung Galaxy S3" did not!
Having installed that driver Kingo Root worked as it promised :)
GCC Canaries
StackGuard: A compiler patch used to guard against stack smashing.
Agile
PMT() Formula For Mortgage With Offset Account
Mortgage repayments are "amortized", which means that the mortgage is payed off with a fixed repayment schedule in regular installments over a period of time [Ref].
Wikipedia has a good explanation for the formula used to calculate monthly amortized loan or mortgage payments. The formula, however, does not apply to mortgages with an offset account.
The following is based on the Wikipedia article. $F$ represents the balance of the offset account.
TODO
Fix FP
Fixed precision floating point we represent a floating-point number using $f$ bits for the fractional component and $i$ bits for the integer component, to make an $N$ bit fixed floating-point number. So for example if we used 4 bits for the integer component and 4 bits for the fractional component we'd write: $$ i_3 \ i_2 \ i_1 \ i_0 \cdot f_{-1} \ f_{-2} \ f_{-3} \ f_{-4} $$ The "dot" is "imaginary" in the sense that we just represent this as a series of bits. To the computer it's just an integer but we are "prentending" it is a floating point number. The unsigned floating point number above has the value defined by the following, as far as we're concerned. $$ i_3*2^3 + i_2*2^2 + i_1*2^1 + i_0*2^0 + f_{-1}*2^{-1} + f_{-2}*2^{-2} + f_{-3}*2^{-3} + f_{-4}*2^{-4} $$ However, as far as the computer is concerned this is just an integer with the value, $$ x_{i_3}*2^7 + x_{i_2}*2^6 + x_{i_1}*2^5 + x_{i_0}*2^4 + x_{f_{-1}}*2^3 + x_{f_{-2}}*2^2 + x_{f_{-3}}*2^1 + x_{f_{-4}}*2^0 $$ So, we get from the computer's idea of the value to our "imagined" decimal by dividing by $2^{4}$. More generally, if there are $f$ fractional bits, we are dividing by $2^{f}$.
Thus, to generically go from the computer's idea of an $N = i+f$ bit integer to our decimal value, we do this: $$ U(i, f) = \frac{1}{2^f}\Sigma{n=0}{N-1}2^nx_n $$ Note that this is for an unsigned type because the ${N-1}_{\text{th}}$ bit does not denote the sign of the value - the value is always +ve.
So, what about negative numbers? Two's complement! To the computer a signed N bit integer will have the following value. $$ \text{value} = -2^{N-1}x_{N-1} + \Sigma_{0}^{N-2} 2^nx_n $$ This formula, describing how two's complement works also tells us why we often see two's complement shown as a circle. When the most significant bit is set we are at the most negative number. As we add 1 we get less negative numbers until all bits are set and we have -1. Adding another 1 and we get zero (the addition overflows so the left-most bit which would have made us negative is lost) and so on...
So, if we are using $f$ bits for the fractional component we do the following to get the fractinal value. $$ S(i, f) = \frac{1}{2^f}\left(-2^{N-1}x_{N-1} + \Sigma_{0}^{N-2} 2^nx_n\right) $$
Using the fact that we are just dividing by $2^f$ we can easily determine the ranges of $U(i, f)$ and $S(i, f)$.
An unsigned number ranges from $0$ to $2^{N-1}$, so $U(i, f)$ must range from $0$ to $\frac{2^{N-1}}{2^f}$.
BitBucket API v2
https://developer.atlassian.com/bitbucket/api/2/reference/resource/repositories/%7Bworkspace%7D/%7Brepo_slug%7D/pullrequests/%7Bpull_request_id%7D/comments/%7Bcomment_id%7D
https://confluence.atlassian.com/bitbucket/app-passwords-828781300.html
https://bitbucket.org/novocien/howto/src/master/?_ga=2.186546081.981859681.1582201564-275772548.1563959193
From Bash:
BITBUCKET_REPO_OWNER=...
BITBUCKET_WORKSPACE=...
BITBUCKET_REPO_SLUG=...
APP_PASSWORD=...
APP_NAME=...
PR_NUMBER
curl -v \
"https://${BITBUCKET_REPO_OWNER}:${APP_PASSWORD}@api.bitbucket.org/2.0/ repositories/${BITBUCKET_WORKSPACE}/${BITBUCKET_REPO_SLUG}/pullrequests /${PR_NUMBER}/comments" \
--header "Content-Type: application/json" \
--request POST \
--data '{ "content" : { "raw": "The comment text" }, "inline" : { "to": 101, "path": "path/to/file.txt" } }'
remove the "inline" section to make it a general comment at the top of the PR
Also easy in Python:
import requests
from getpass import getpass
BITBUCKET_REPO_OWNER="..."
BITBUCKET_WORKSPACE="..."
BITBUCKET_REPO_SLUG="..."
APP_PASSWORD="..."
APP_NAME="..."
PR_NUMBER=123
LINE_NO=123
url = F'https://{BITBUCKET_REPO_OWNER}:{APP_PASSWORD}@api.bitbucket.org/2.0/ repositories/{BITBUCKET_WORKSPACE}/{BITBUCKET_REPO_SLUG}/pullrequests/{PR_NUMBER}/comments'
mydata = { "content" : { "raw": "Hello Python" },
"inline" : { "to": LINE_NO, "path": "path/to/file.txt" } # "from" : 122 also poss for line range
}
x = requests.post(url, json = mydata)
print("\n\nREQUEST:\n")
print(x.request.headers)
print(x.request.body)
print("\n\nRESPONSE:\n")
print(x.status_code, x.reason, x.url)
pp.pprint(x.json())
Conferences
https://www.embedded-world.eu https://events.linuxfoundation.org/events http://2019.pyconuk.org/
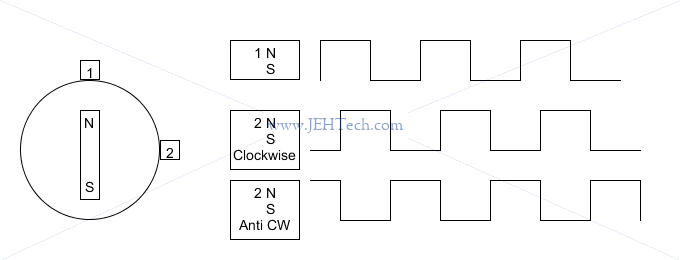
Magnetic Rotary Encoder
EU
https://fullfact.org/europe/eu-facts-behind-claims-uk-influence/ https://www.theguardian.com/politics/datablog/2015/oct/19/simon-hix-is-the-uk-marginalised-in-the-eu https://www.theguardian.com/world/datablog/2015/nov/02/is-uk-winner-or-loser-european-council https://www.thomsonreuters.com/en/press-releases/2017/march/eu-laws-introduced-in-the-uk-highlights-scale-of-challenge-facing-lawmakers-following-brexit.html https://blogs.lse.ac.uk/europpblog/2016/06/21/is-the-eu-really-run-by-unelected-bureaucrats/
Hexdump Program
cat firmware.bin | hexdump -v -e '1/1 "0x%02X, "'